In the realm of technology, quantum computing stands as a formidable frontier, promising unprecedented computational power and the potential to revolutionize various fields. One domain where its impact looms large is cryptography – the art of secure communication.
Quantum computers, with their unique parallelism capability, can execute tasks such as factoring large numbers, simulating quantum systems, and optimizing complex algorithms with unparalleled efficiency. For instance, quantum computers can swiftly crack a 2048-bit public key encryption that would take classical computers a few million years to decipher. This poses both challenges and opportunities in the field of cybersecurity. Let’s delve into the complexities of quantum computing and explore its profound impact on cryptography.
Understanding Quantum Computing
Quantum computing solutions has two fundamental principles
- Superposition - A fundamental principle in quantum mechanics where a quantum system can exist in multiple states simultaneously, represented by a combination of classical states.
- Entanglement - A phenomenon where the quantum states of two or more particles become interconnected, even when separated by vast distances, leading to correlated behavior that defies classical intuition.
Unlike classical bits, which represent either a 0 or a 1, quantum bits or qubits can exist in a state of superposition, embodying both 0 and 1 simultaneously. This unique property enables quantum computers to perform a multitude of calculations simultaneously, exponentially increasing computational capacity. Additionally, qubits can be entangled, meaning the state of one qubit is directly correlated with the state of another, regardless of the distance between them.
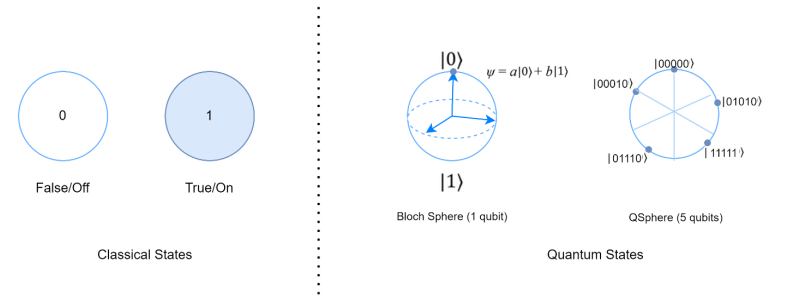
Unveiling the Power of Quantum Computing
The superposition property enables a quantum computer to be in multiple states at once. By harnessing this feature, a quantum computer with n qubits can represent and process 2n states simultaneously, exploiting the vast landscape of possibilities in parallel. With this unique capability, a quantum computer unlocks the power of exponential growth. A quantum computer with 300 qubits can, in theory, represent a greater number of states than there are particles in the observable universe.
Roadblocks Awaiting Breakthroughs
Despite its promise, quantum computing impacts significant hurdles on the path to fruition. One of the foremost challenges is mitigating errors inherent in quantum systems. The delicate nature of qubits renders them susceptible to environmental interference and decoherence, leading to the collapse of superposition upon measurement. Overcoming these obstacles demands groundbreaking advancements in error correction and fault-tolerant quantum computing architectures.
Impact on Cryptography
Shor’s algorithm, a technique proposed by Peter Shor in 1990, describes how a suitably powerful quantum computer could very quickly find the prime factors of large numbers, a task that classical computers find extremely difficult. RSA encryption relies on this very challenge to protect data being shuttled around online.
The Public-Private Key scheme (PPK) is the backbone of today’s cryptographic protocols. Applications such as data encryption, authentication, digital signatures, privacy-preserving computing, cryptographic hash functions, etc., are all based on PPK.
The hypothetical “Q-day” – the day when a quantum computer with enough power can swiftly dismantle existing cryptographic safeguards – could potentially wreak havoc on the digital world. Its scale of impact could only be compared to what the Y2K problem threatened to do. Cybersecurity experts don’t all agree on when this day will arrive. Some researchers predict that “Q-Day” will come sometime in the middle of the century. Others think it’s set to arrive much sooner, with few suggesting it might come as early as 2025.
In response, the global community is fervently exploring post-quantum cryptography (PQC) solutions that are resilient against quantum threats. PQC algorithms, such as lattice-based and hash-based cryptography, offer promising avenues for safeguarding sensitive information in the quantum era.
Government agencies are leading the preparations, with NIST announcing the first four quantum-resistant encryption algorithms and the US Congress passing a law that enforces federal agencies to prepare their migration to quantum-secure cryptography. At the same time private sector is not behind with startups like QuSecure™ and QRC™ offering comprehensive platforms & solutions.
Embracing the Quantum Future with Innovation Labs 2.0
As the race toward quantum supremacy accelerates, businesses and governments alike are poised to capitalize on the transformative potential of quantum computing. At Jade, our commitment to innovation extends beyond the present, with our ILabs 2.0 positioned as a vanguard against the evolving landscape of technology. By staying ahead of the curve and on top of upcoming trends, threats, and opportunities, our team ensures that our customers navigate the quantum era with confidence. Rigorous exploration of emerging technologies, proactive threat analysis, and strategic identification of opportunities form the core of our R&D endeavors. By doing so, we not only equip our customers with cutting-edge solutions but also empower them to embrace the quantum future with a comprehensive understanding of the digital terrain.